What Is Two Factor Authentication In Cyber Security - Worksheets are now essential tools utilized in a variety of tasks, including education and learning, commerce, and individual management. They give structured layouts that support understanding, strategizing, and decision-making across various degrees of complexity, from standard math problems to detailed service evaluations.
Why And How To Use Two factor Authentication

Why And How To Use Two factor Authentication
Worksheets are developed records that aid prepare information, info, or tasks in an organized fashion. They provide an aesthetic method to present ideas, enabling individuals to get in, take care of, and examine information successfully. Whether in educational settings, business meetings, or personal usage, worksheets simplify treatments and improve efficiency.
Worksheet Varieties
Discovering Tools for Children
Worksheets are extremely beneficial tools for both educators and pupils in academic atmospheres. They include a variety of activities, such as mathematics projects and language tasks, that allow for method, reinforcement, and examination.
Printable Business Equipments
In the world of entrepreneurship, worksheets play a versatile function, satisfying various needs such as financial planning, project administration, and data-driven decision-making. They aid businesses in developing and checking budget plans, devising task strategies, and conducting SWOT evaluations, inevitably helping them make well-informed options and track developments towards set objectives.
Individual Task Sheets
Individual worksheets can be a useful device for achieving success in different elements of life. They can assist people established and work in the direction of goals, handle their time effectively, and check their progress in locations such as physical fitness and finance. By offering a clear structure and feeling of liability, worksheets can help individuals remain on track and achieve their purposes.
Advantages of Using Worksheets
The advantages of using worksheets are manifold. They advertise active discovering, improve understanding, and foster critical reasoning abilities. Additionally, worksheets motivate company, boost performance, and promote partnership when used in team settings.
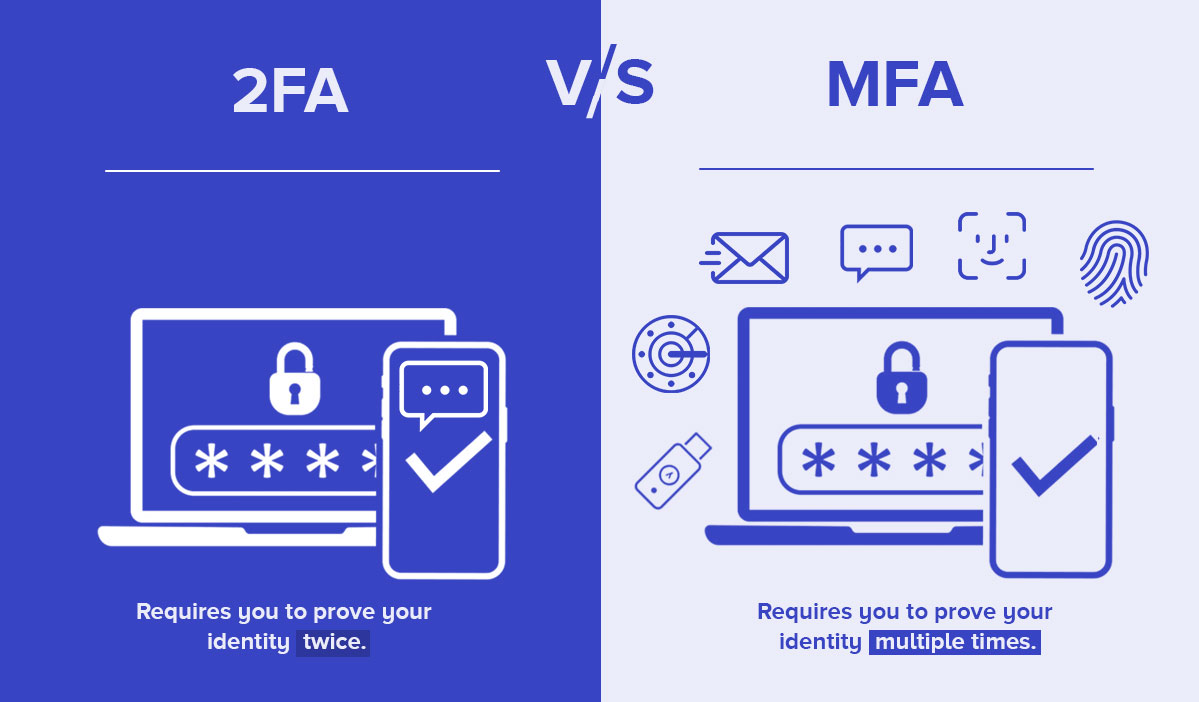
Two Factor Vs Multifactor Authentication What s The Difference

How To Hack Two Factor Authentication

Layer Up Your Account Security With Multi Factor Authentication MFA
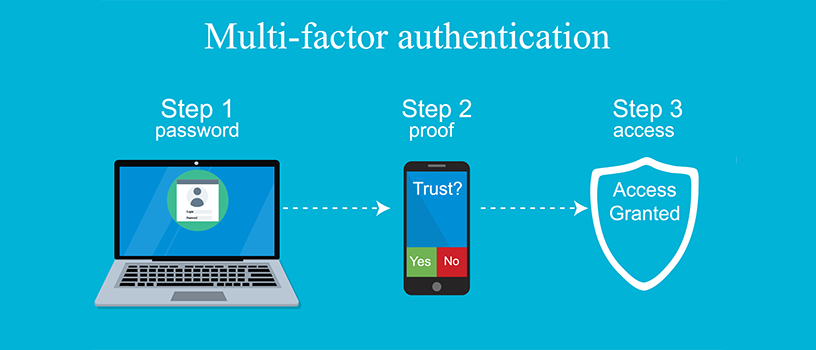
Multifactor Authentication The University Of Akron Ohio

What Is Two Factor Authentication
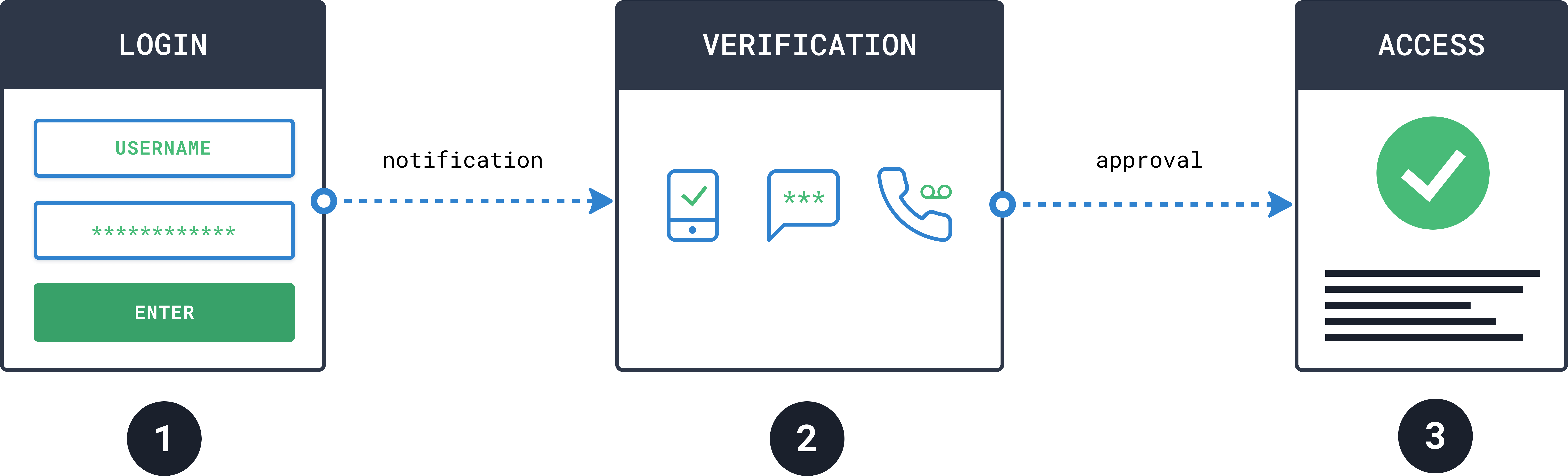
Two Factor Authentication

What Best Describes Two Factor Authentication For A Credit Card Using

What Is Multi Factor Authentication MFA Cisco
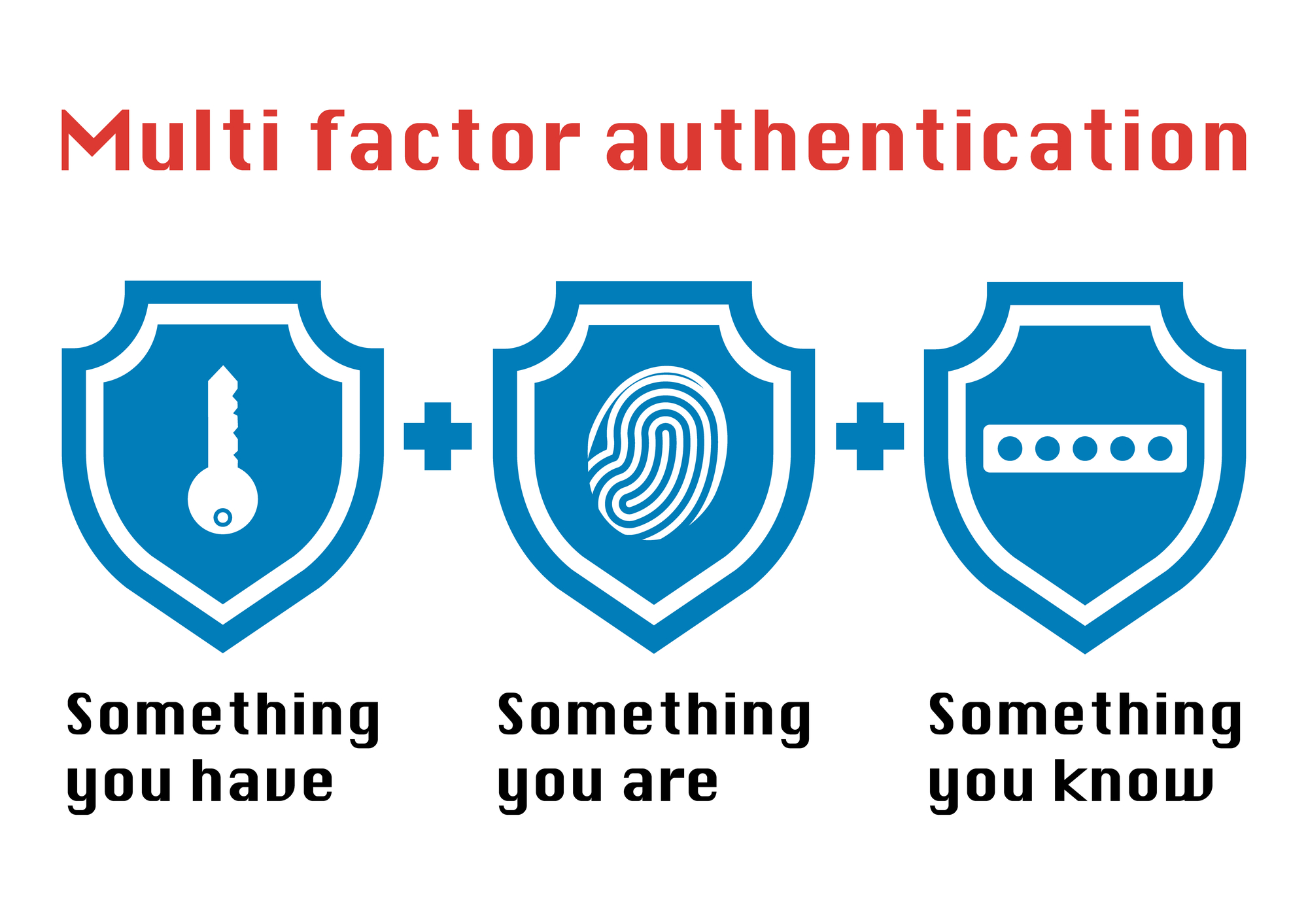
Multi Factor Authentication Basics And How MFA Can Be Hacked PCH

What Is Two Factor Authentication 2FA And Do You Need It