Two Factor Authentication In Computer Security - Worksheets are currently vital instruments utilized in a variety of activities, consisting of education and learning, business, and personal administration. They provide structured layouts that sustain understanding, planning, and decision-making throughout various degrees of intricacy, from standard math issues to elaborate organization evaluations.
Why And How To Use Two factor Authentication

Why And How To Use Two factor Authentication
Worksheets are organized documents that help methodically set up details or jobs. They give a visual depiction of concepts, allowing users to input, handle, and evaluate information successfully. Whether made use of in school, meetings, or personal setups, worksheets streamline procedures and boost effectiveness.
Worksheet Varieties
Educational Worksheets
Worksheets play an important role in education and learning, serving as important tools for both educators and trainees. They encompass a range of activities such as math problems and language tasks, enabling method, reinforcement, and evaluation.
Business Worksheets
Worksheets in the business round have different objectives, such as budgeting, project administration, and evaluating data. They help with educated decision-making and surveillance of goal accomplishment by companies, covering economic reports and SWOT analyses.
Individual Activity Sheets
On a personal level, worksheets can aid in goal setting, time monitoring, and practice monitoring. Whether intending a budget, organizing an everyday timetable, or keeping an eye on health and fitness development, personal worksheets provide framework and responsibility.
Maximizing Discovering: The Advantages of Worksheets
Worksheets provide various advantages. They boost engaged understanding, boost understanding, and support logical thinking capacities. Furthermore, worksheets support structure, rise performance and allow synergy in team circumstances.

Layer Up Your Account Security With Multi Factor Authentication MFA
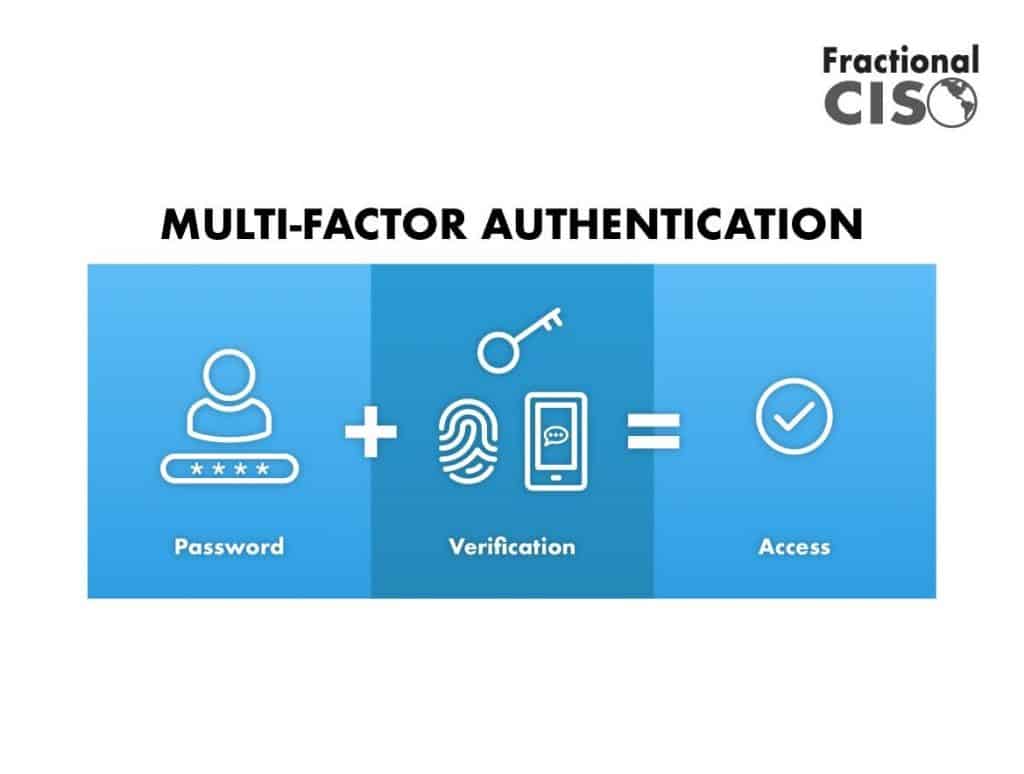
Multi Factor Authentication Problems Riset

Multi Factor Authentication Cyber Security M Tech Systems

How To Hack Two Factor Authentication

How To Secure Remote Access To A Cisco Device
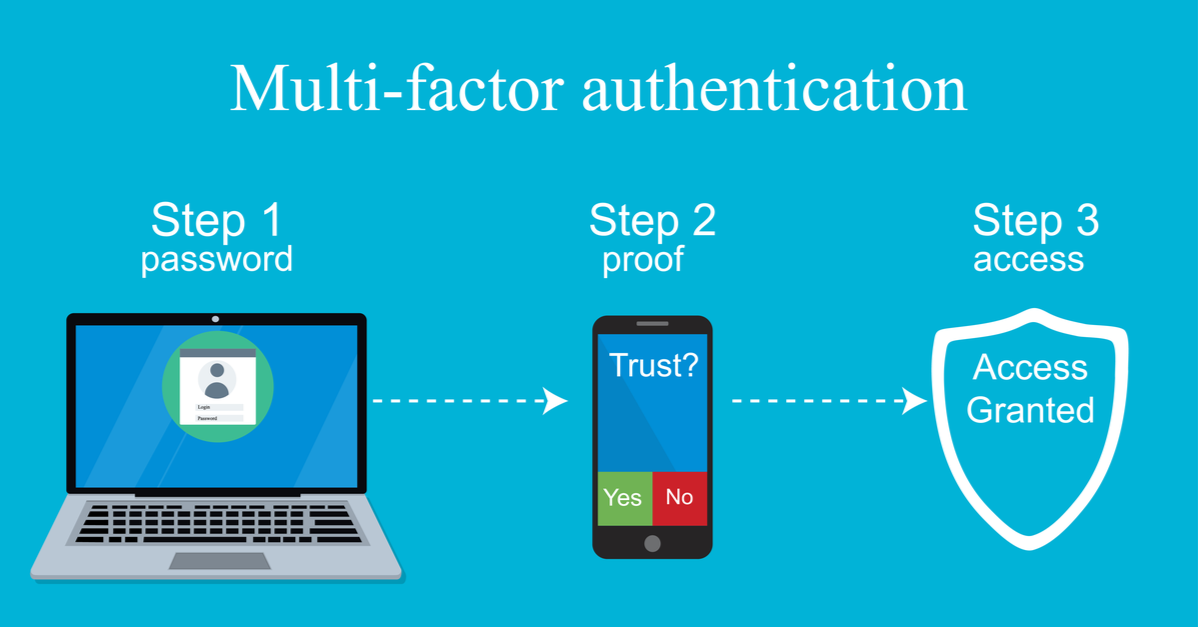
Multi Factor Authentication Is Not An Option Data Command

Two factor Authentication For Beginners

2fa Explained How To Enable It And How It Works ITworld

What Is Multi Factor Authentication MFA Concensus Technologies
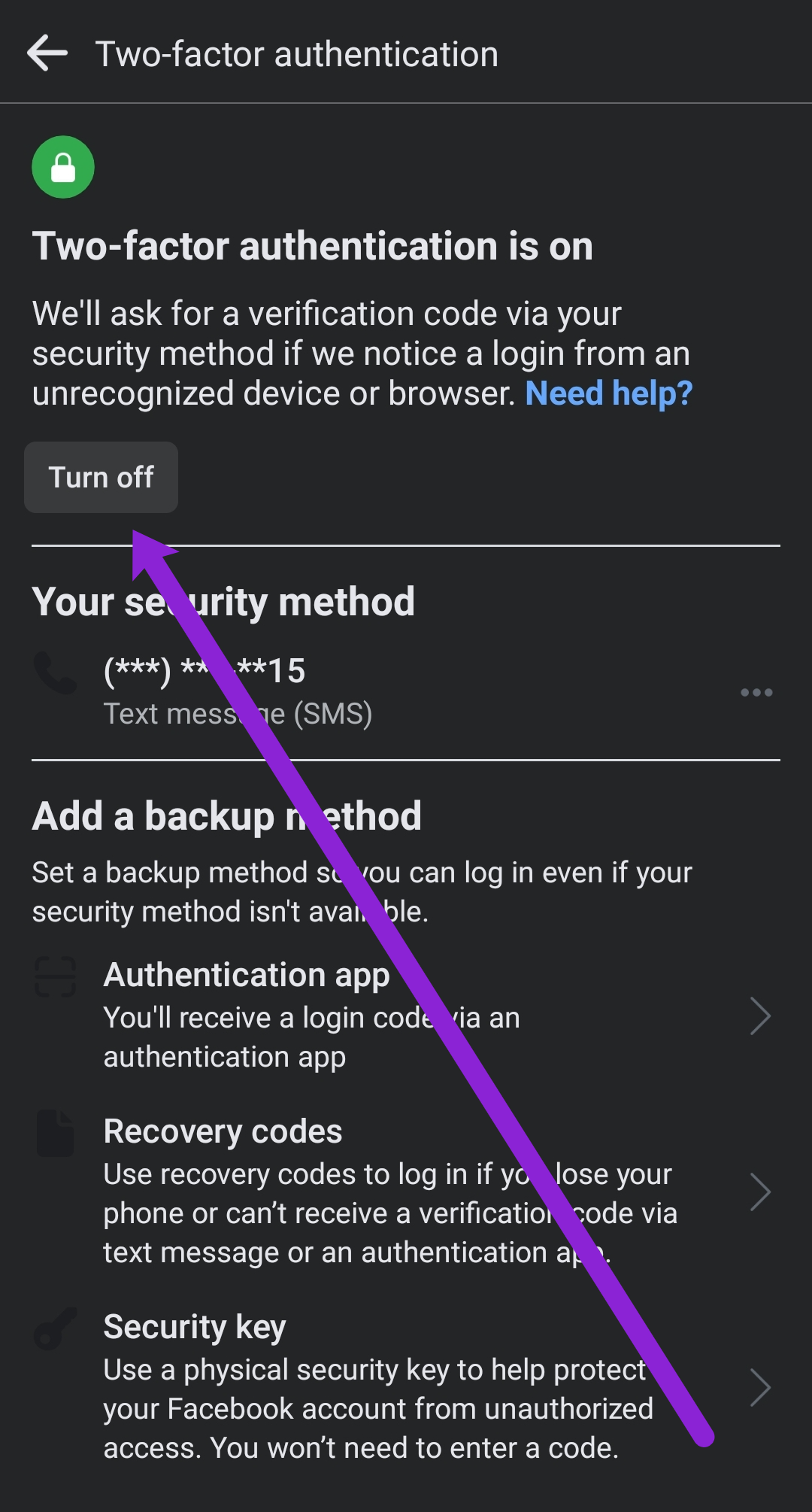
Security Checks Preventing Login Facebook 2022 Login Pages Info