2 factor authentication cyber security SMS verification SMS or text messaging can be used as a form of two factor authentication when a message is sent to a trusted phone number The user is prompted to either interact with the text or use a one time code to verify their identity on a site or app
Step 1 The user opens the application or website of the service or system they want to access They are then asked to log in using their credentials Step 2 The user enters their login credentials which will typically be their username and password Latest Blogs
2 factor authentication cyber security

2 factor authentication cyber security
https://arrix.nl/wp-content/uploads/2020/05/2-factor-authentication-1536x1024.jpg
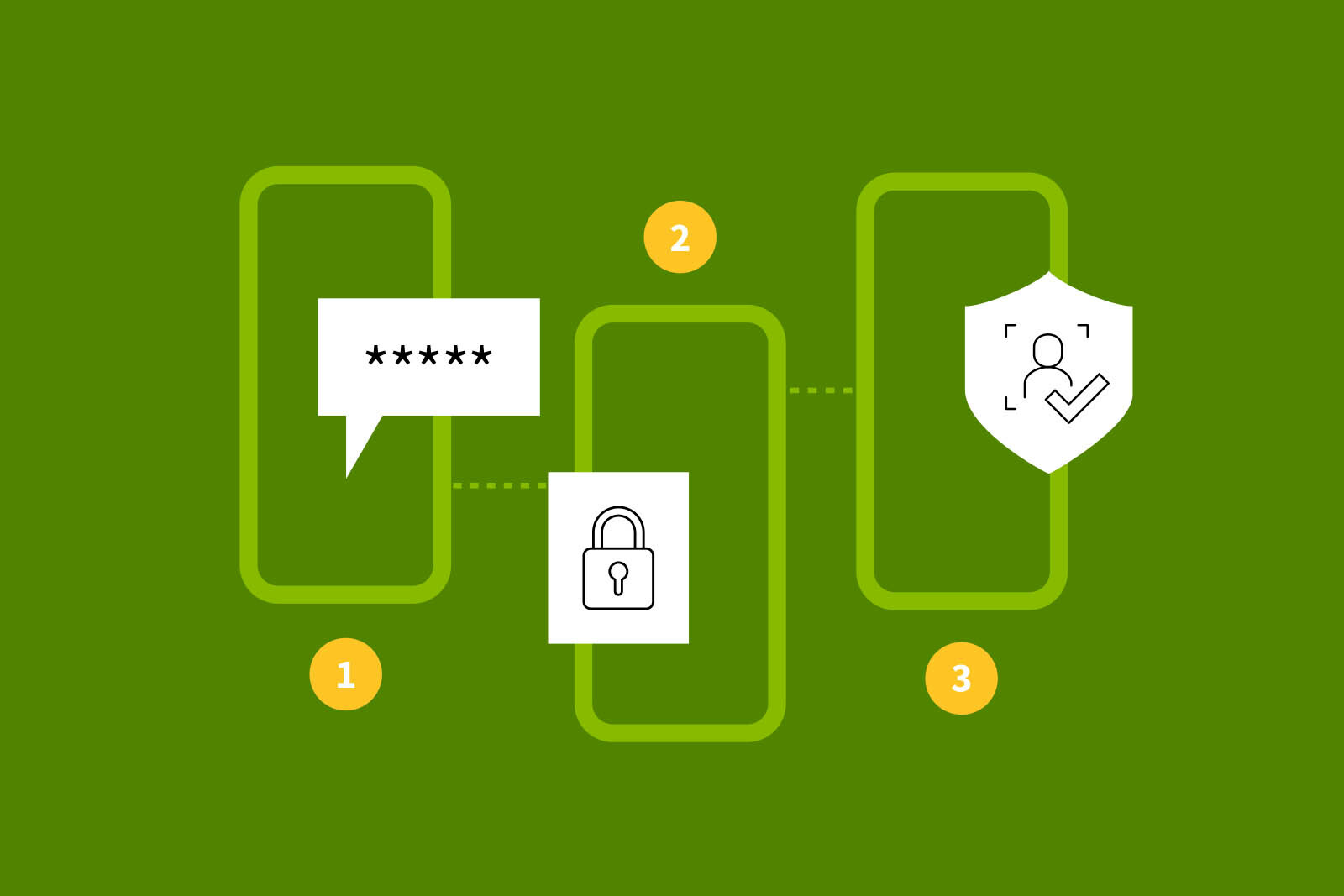
Multi Factor Authentication Enhances Cybersecurity
https://imgix.doingmoretoday.com/app/uploads/2022/09/03085837/Multi-Factor-Authentication-Diagram-For-Enhanced-Cybersecurity.jpg

Increase Cyber Security With Two Factor Authentication CCSI
https://ccsitx.com/wp-content/uploads/2018/10/1_LAiTdpODah4fuG_xb0nNTg.jpg
Learn More Gaining credentials allows attackers to impersonate the account owner and appear as someone who has legitimate access such as an employee contractor or third party supplier Learn how MFA can strengthen user authentication Credential Theft An Adversary Favorite Multi factor authentication vs two factor Products Services Security What Is Two Factor Authentication 2FA Two factor authentication 2FA strengthens access security with an extra authentication method added to a username and password A common example of 2FA is a smartphone app that requires users to approve their authentication request before logging in Watch 2FA
Blog What Is Two Factor Authentication 2FA Teju Shyamsundar Senior Product Marketing Manager July 19 2021 Solution Resources Why is Two Factor Authentication Needed Traditional password based authentication systems are vulnerable to phishing attacks and the use of weak or reused passwords
More picture related to 2 factor authentication cyber security

Multi Factor Authentication Cyber Security M Tech Systems
https://www.mtechsystems.co.uk/wp-content/uploads/2019/08/M-Tech-Multi-Factor-Authentication-e1565086481971-1536x1086.jpg
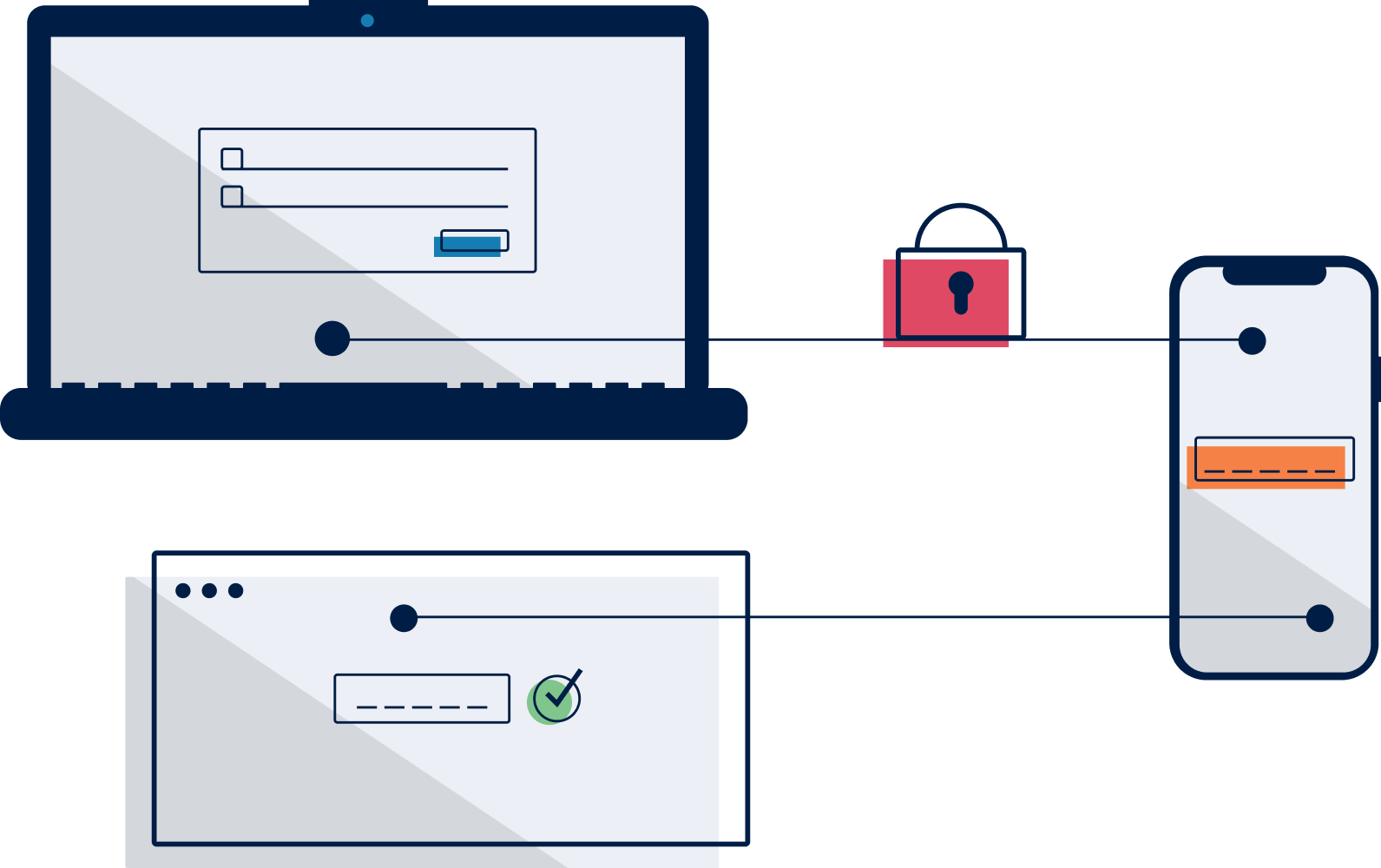
Turn On Multi factor Authentication Cyber gov au
https://www.cyber.gov.au/sites/default/files/2023-02/two-factor-authentication-graphic.png

Boost Security With Multi Factor Authentication Complete Technology
https://www.completetechnology.com/wp-content/uploads/2023/01/Use-Multi-Factor-Authentication-to-Improve-Cybersecurity-Complete-Technology-Services.jpg
So let s dive in What is two factor authentication Two factor authentication often referred to as two step authentication and 2FA is a method for keeping your data safe online by adding Two factor authentication 2FA Two factor authentication typically comes in the form of a passcode sent to a mobile device phone number or email sometimes referred to as a one time PIN OTP Multi factor authentication MFA
GRC A Guide to Two Factor Authentication 2FA James MacKay Cyber Security Awareness MetaBlog about the author James MacKay is the COO of MetaCompliance and a recognised security awareness training expert Some thing you know This can be a pass word PIN code or an answer to a personal question for instance Some thing you have In this case you will need a physical object for identifying your self such as your phone or credit card There are even physical security keys used for multi factor authentication Some thing you are

Cybersecurity For Small Businesses Without Breaking The Bank
https://itchronicles.com/wp-content/uploads/2020/09/two-factor-authentication-security.jpg
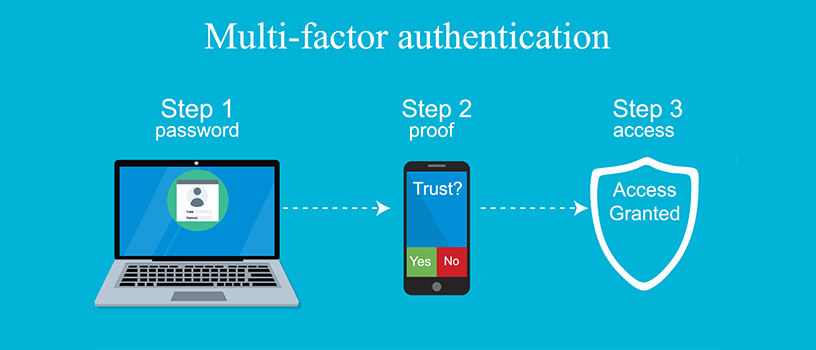
Multi factor Authentication Is A Powerful Tool Against Cyberattacks
https://2wtech.com/wp-content/uploads/2021/07/mfa-blog.png
2 factor authentication cyber security - What makes a good password There are three keys to a good strong password length randomness and uniqueness One easy way to achieve these goals of length randomness and uniqueness is picking three or four common but random words For example your password could be flower lamp green bear which is easy to remember but hard to guess