what is an m2m token M2M Authorization is the process of providing remote systems with secure access to information Using this process business systems can communicate autonomously and execute business functions based on
Learn the differences between Personal Access Tokens PATs Machine to Machine M2M authentication and API Keys and how they can be used If you re building a Machine to machine M2M authentication is the cornerstone of secure seamless communication between interconnected devices and applications It guarantees data security privacy and reliability playing a
what is an m2m token

what is an m2m token
http://www.pantechsolutions.net/wp-content/uploads/2013/08/92-What-is-M2M-Machine-to-Machine-Architecture.png
What Is M2M SIM Card Technology Tech Strange
https://www.techstrange.com/wp-content/uploads/2021/12/What-Is-M2m-Sim-Card-Technology-.jpg
Guide To Crypto Token Types Bitcoin Insider
https://cdn-images-1.medium.com/max/924/0*VPD3dYkRp7VOOVqF.png
The Client Credentials Flow is used by an application to obtain access tokens for itself rather than for a user This is useful in machine to machine use cases such as bots CLIs backend or Machine to machine M2M authentication is the process of verifying digital identities between devices or systems enabling secure and automated interactions without
Machine to machine M2M authentication enables services and applications that run on AWS to securely communicate with one another to access resources and data Instead of using long Machine to Machine M2M Authentication M2M authentication involves verifying the identity of devices or applications communicating over a network This process ensures that only
More picture related to what is an m2m token

This Is An M2M SIM Card
https://uploads-ssl.webflow.com/5ce0f7e10b5f0b6e5e22c314/6330ba46a9082d02df843491_M2M-SIM-Karten-von-whereversim.webp
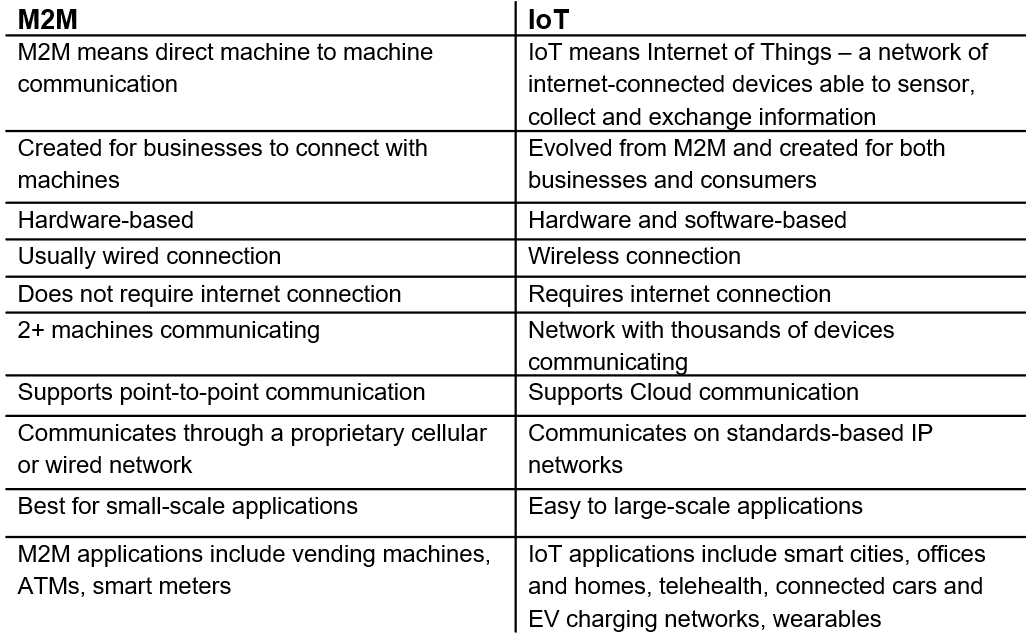
Whats The Difference Between Iot And M2m Images And Photos Finder
https://www.eseye.com/wp-content/uploads/IoT-M2M-Differences-Eseye_.png
What M2M Is And How It s Different From IoT IoT Tech Trends
https://www.iottechtrends.com/assets/uploads/2020/05/Featured-Image-M2M-versus-IoT.jpg
M2M Authorization is the process of providing remote systems with secure access to information Using this process business systems can communicate autonomously and execute business functions based on predefined M2M access tokens In token based authentication non interactive clients provide client id and client secret in a call to the Authentication API token endpoint to get an access token This
Simplify communication between APIs and trusted services Easily handle authentication and authorization for non interactive applications with machine to machine communication from This post is designed to help you decide which approach is best to securely connect your applications either residing on premises or hosted outside of AWS to your AWS
What Is An M2M SIM Card LaptrinhX
https://dz2cdn1.dzone.com/storage/article-thumb/5534684-thumb.jpg

Create And Validate Jwt Token In Java Using Jjwt Viralpatel Net json
https://miro.medium.com/max/5284/1*RvUzEHQi5JEifWCBY4Rkng.png
what is an m2m token - Machine to machine M2M authentication enables services and applications that run on AWS to securely communicate with one another to access resources and data Instead of using long